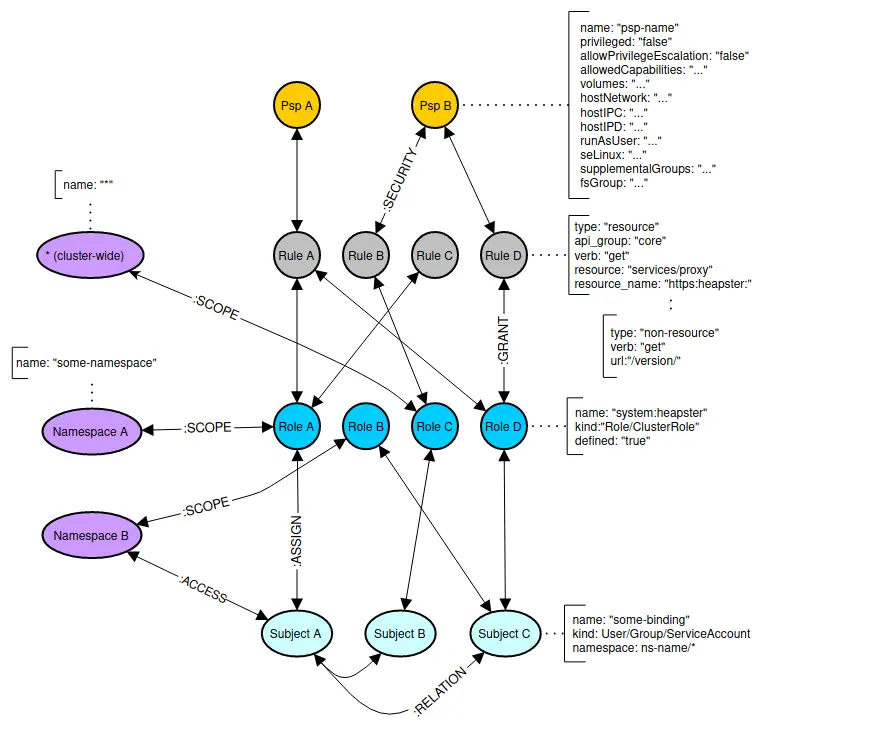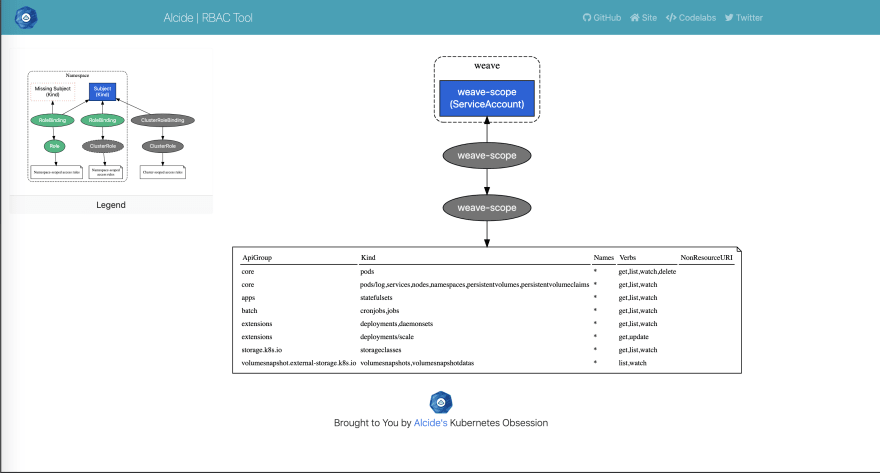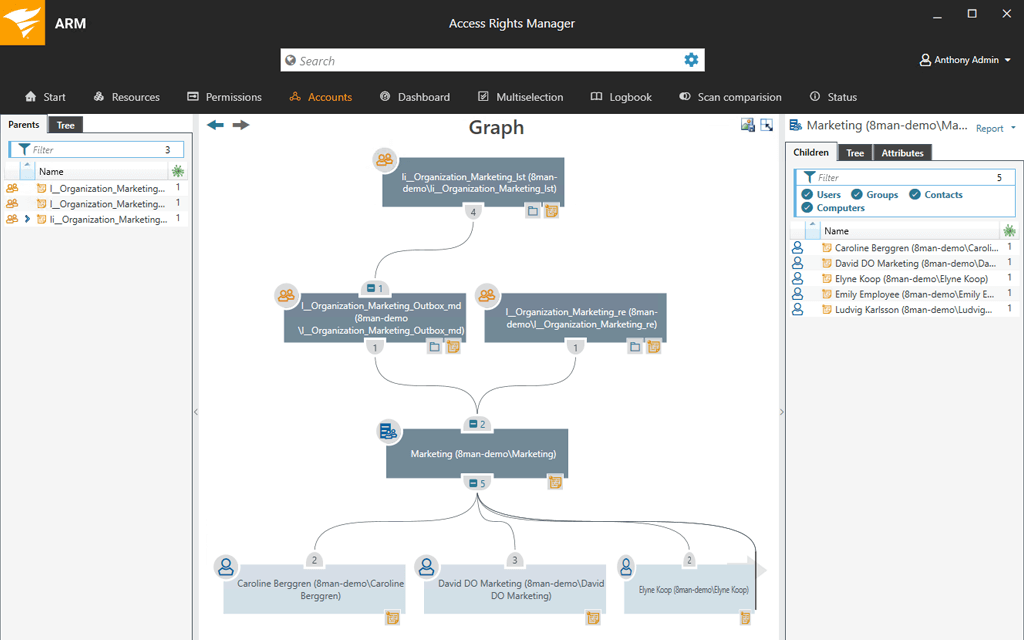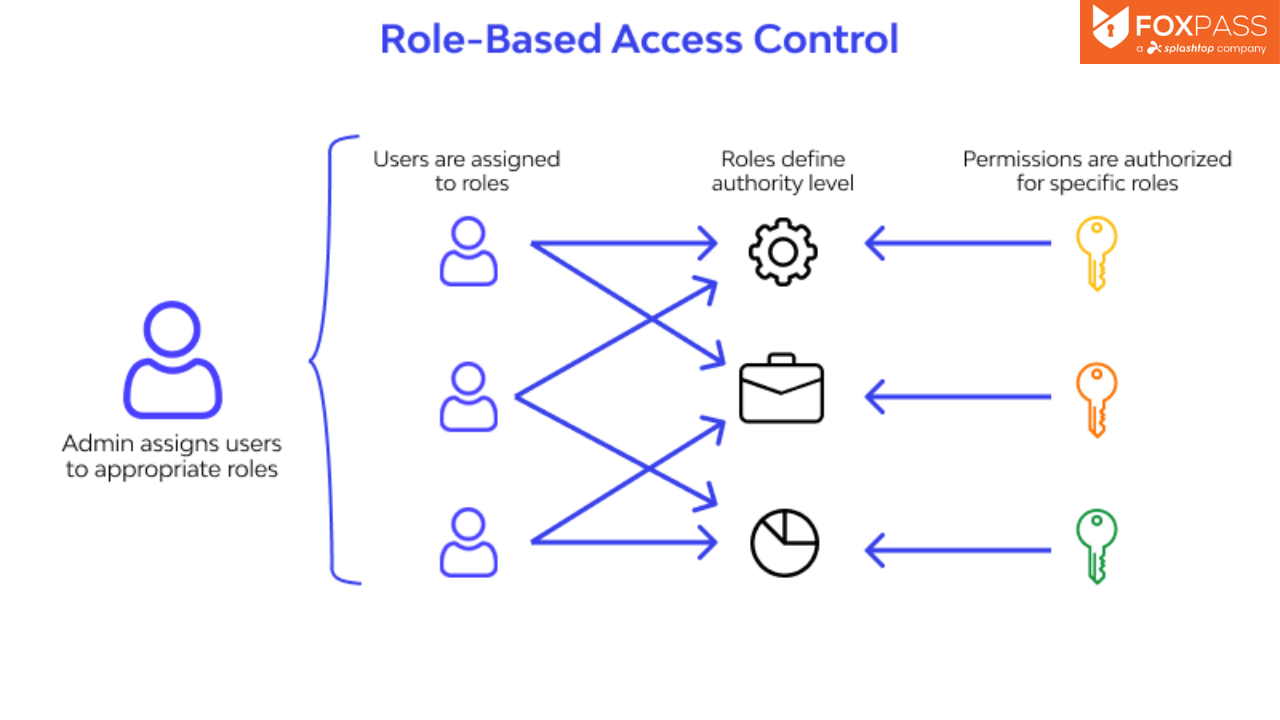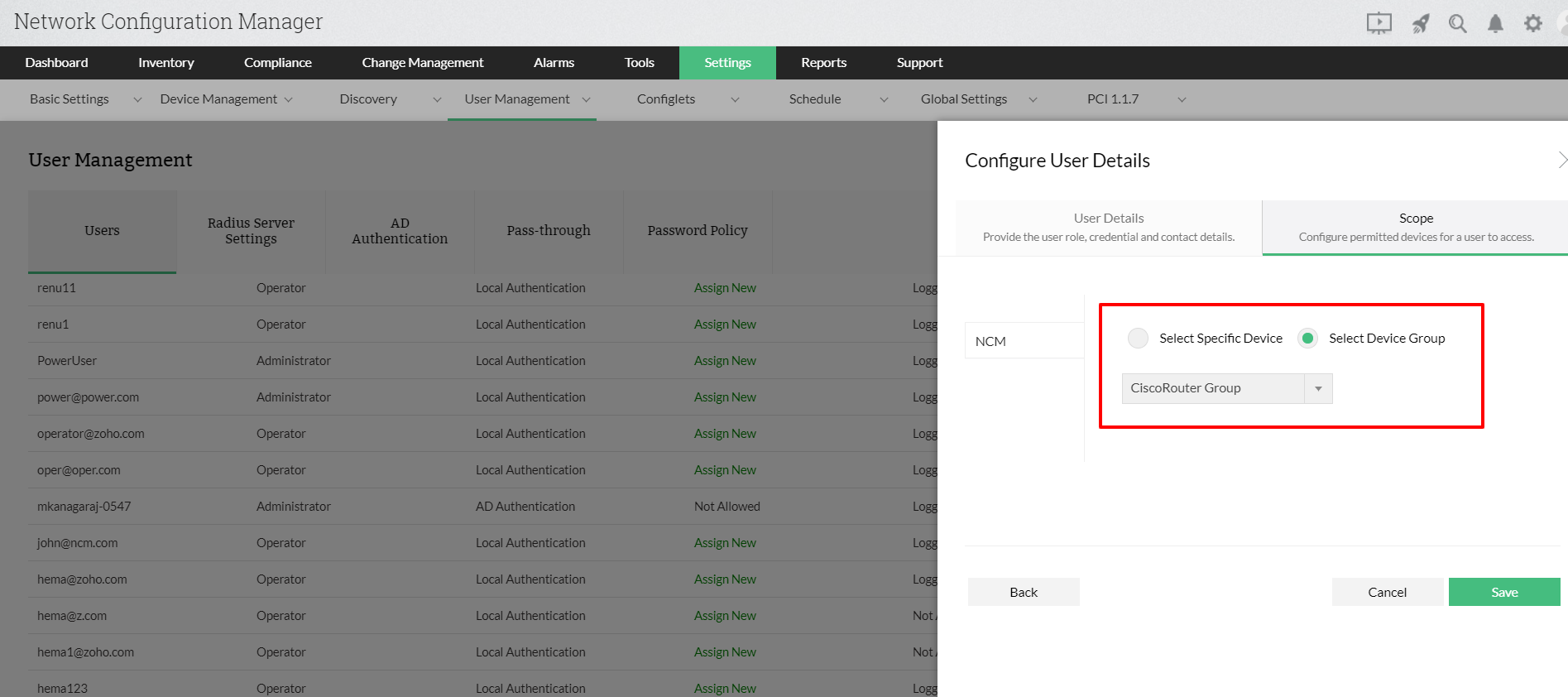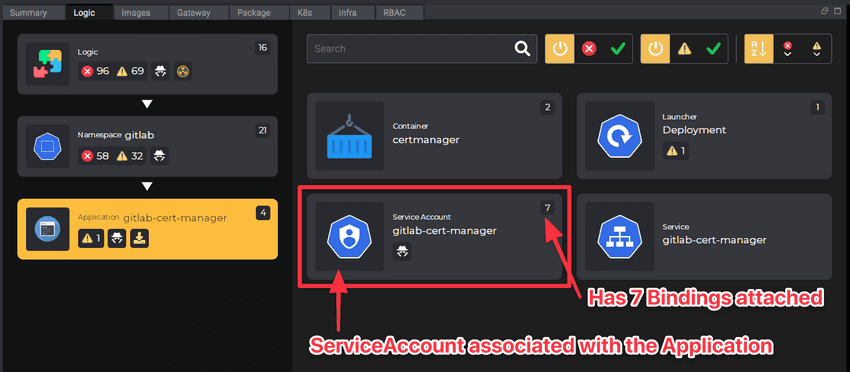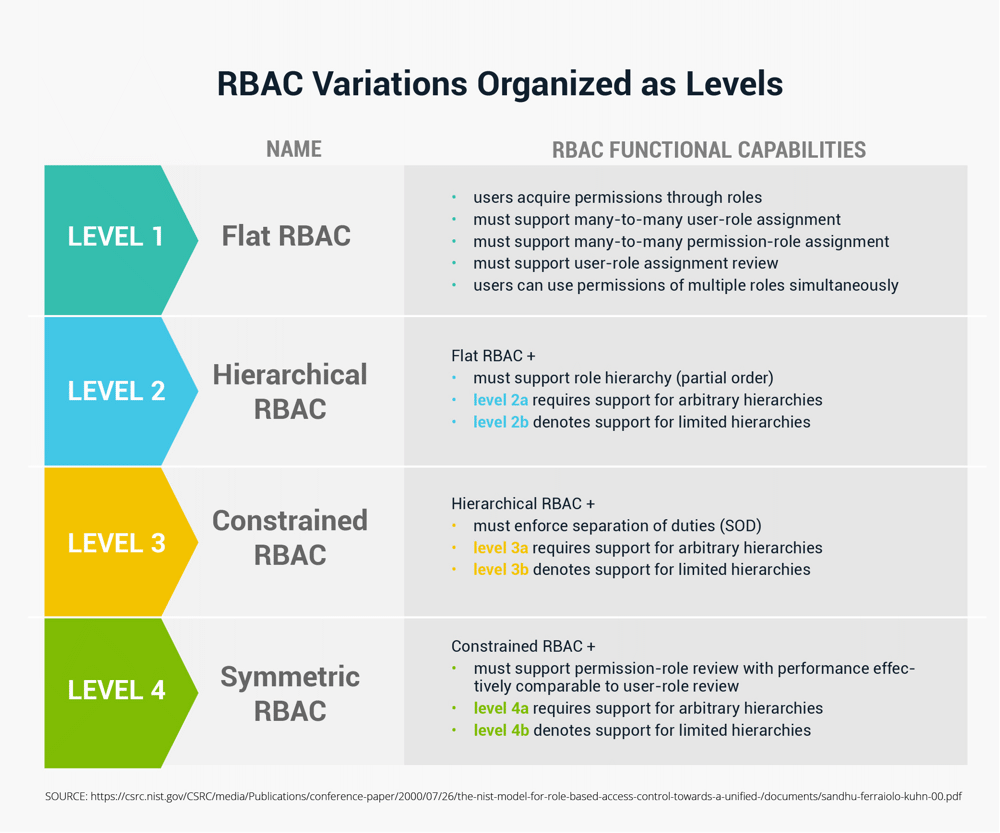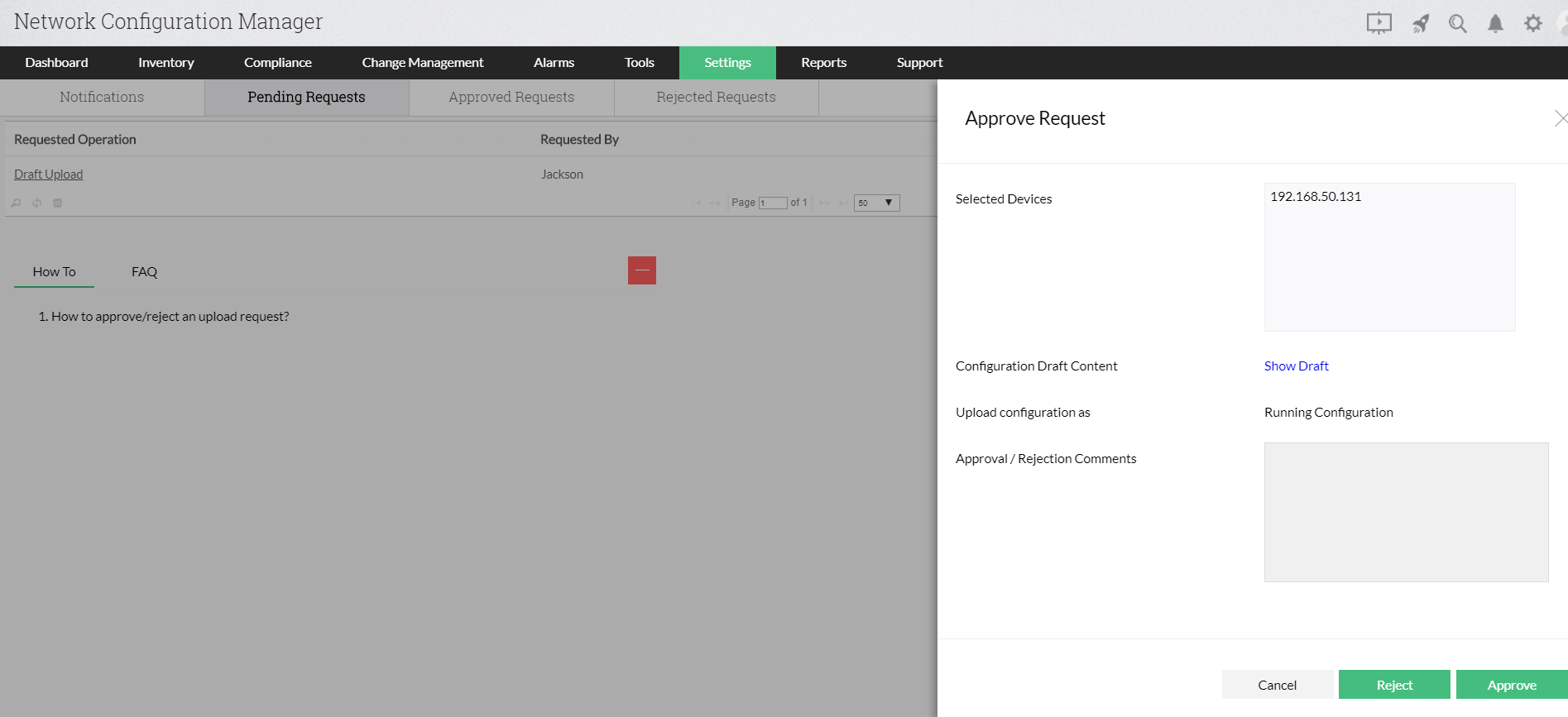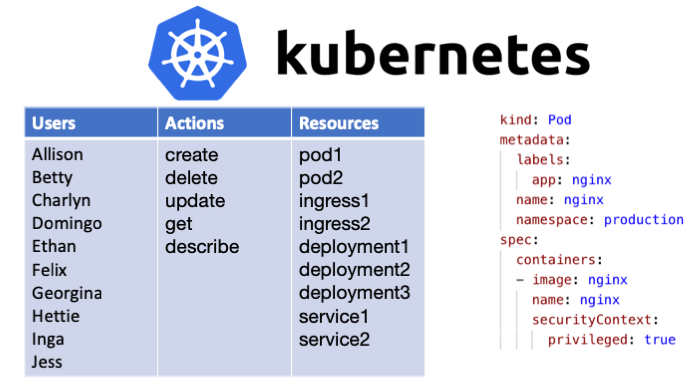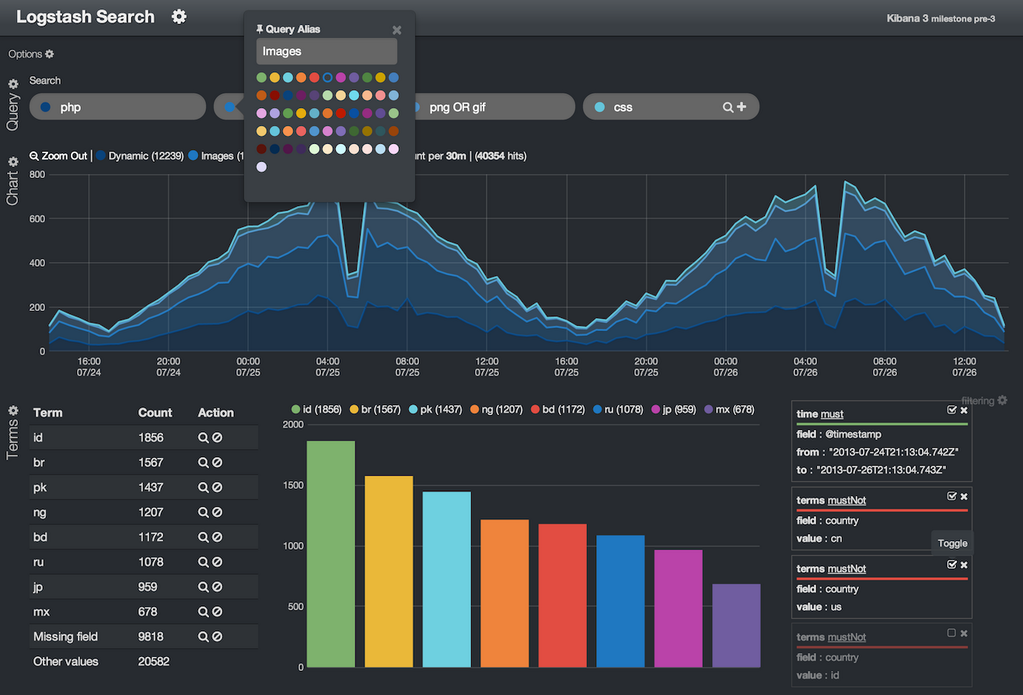
Role Based Access Control (RBAC) in Elastic Stack – BGD e-GOV CIRT | Bangladesh e-Government Computer Incident Response Team

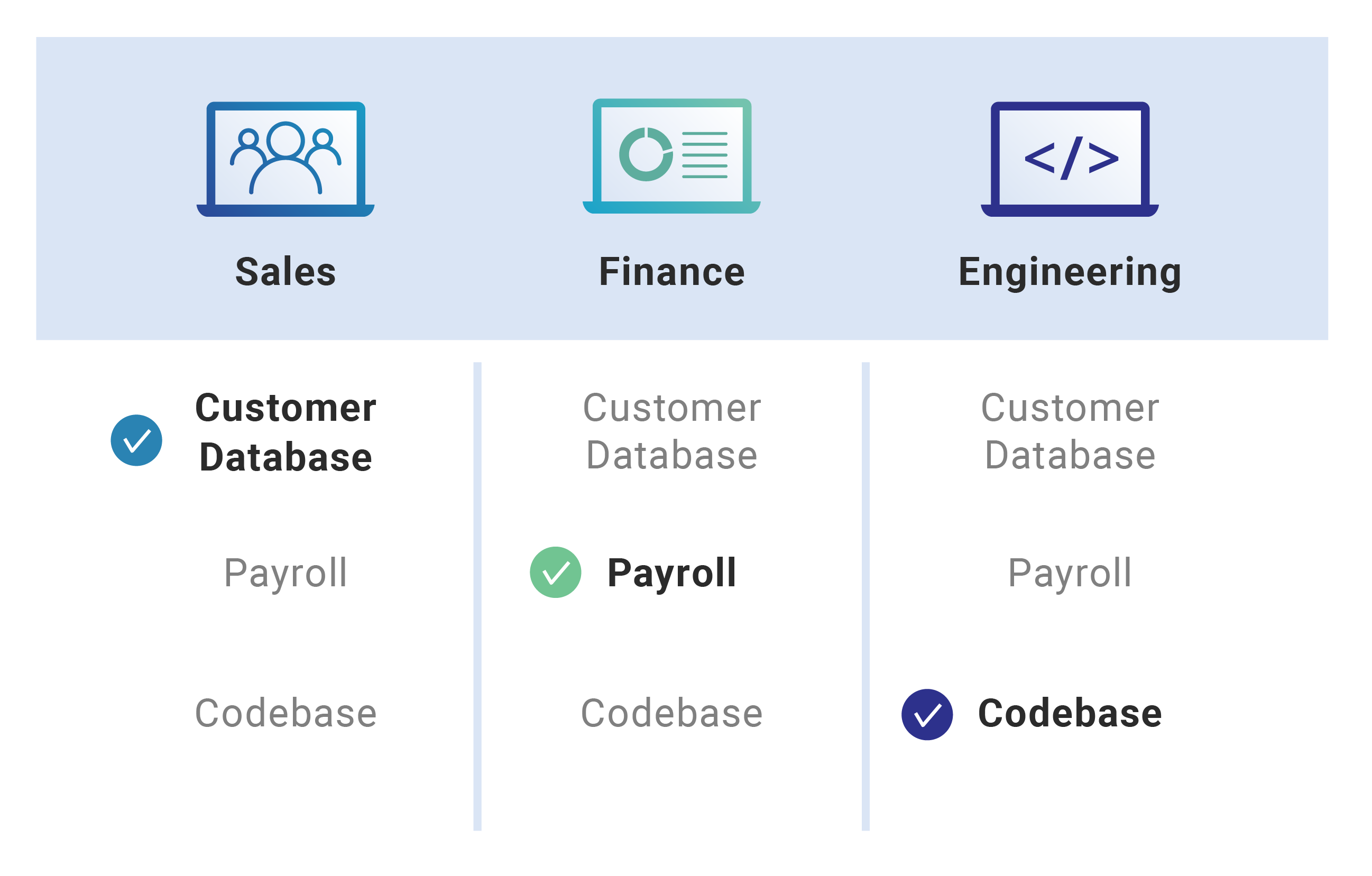
How to Implement fine-grained Role-Based Access Control for Your Infrastructure as Code with Custom RBAC Roles | env0