Information | Free Full-Text | Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things

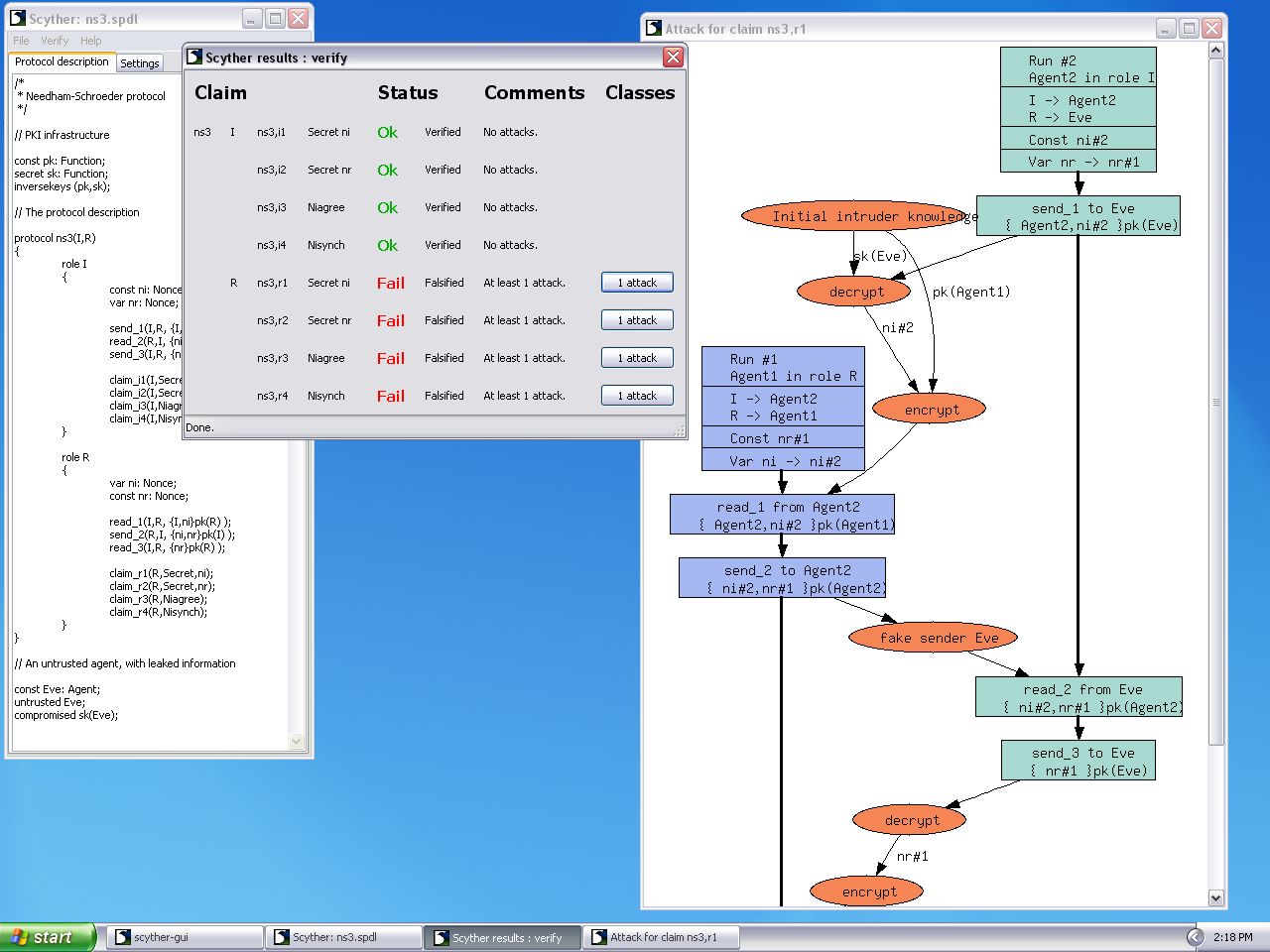
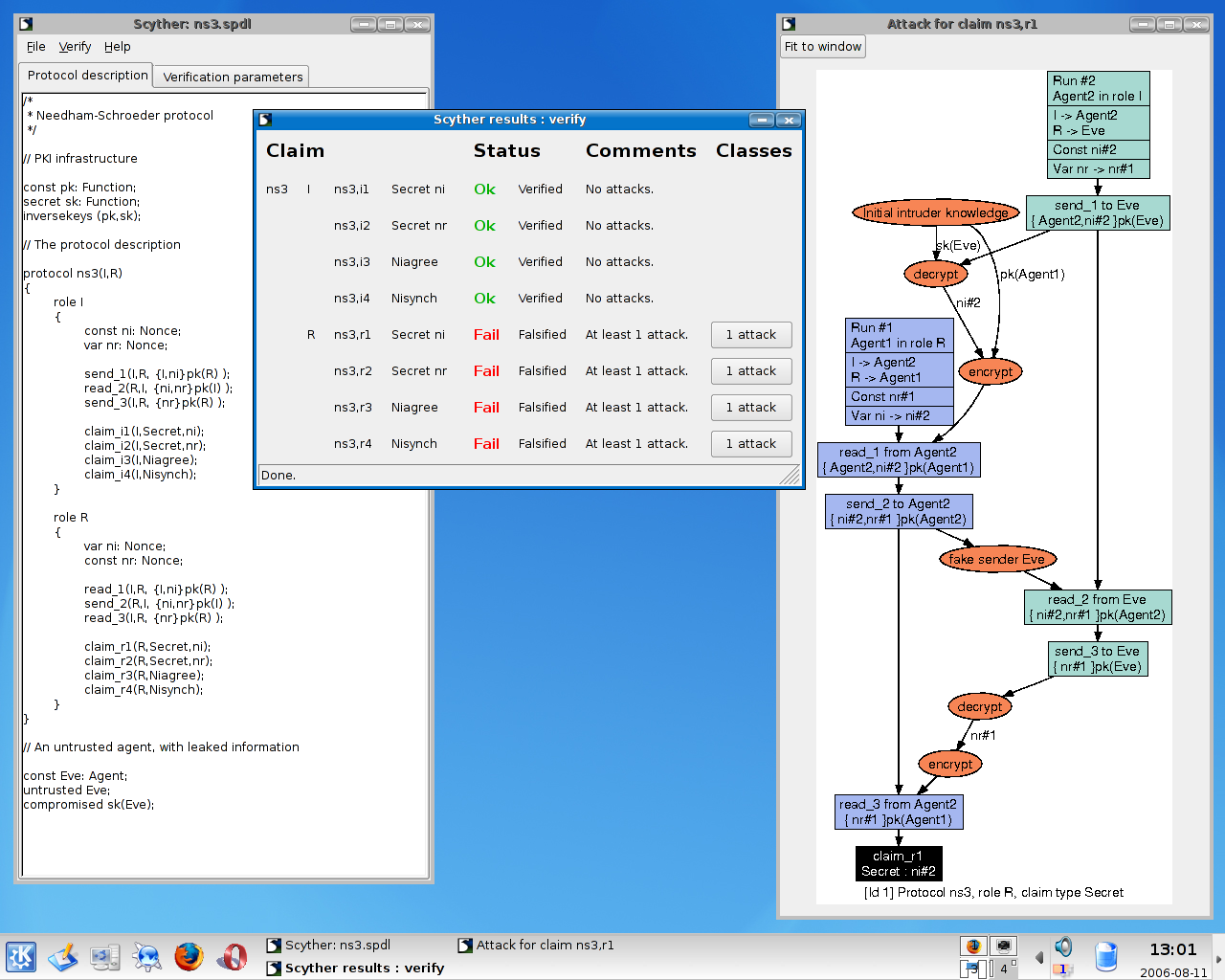
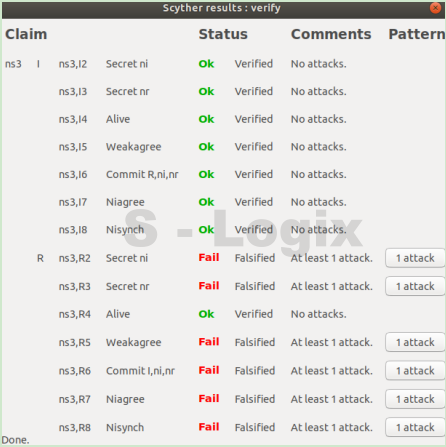
PDF) Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Hazem A . Elbaz - Academia.edu

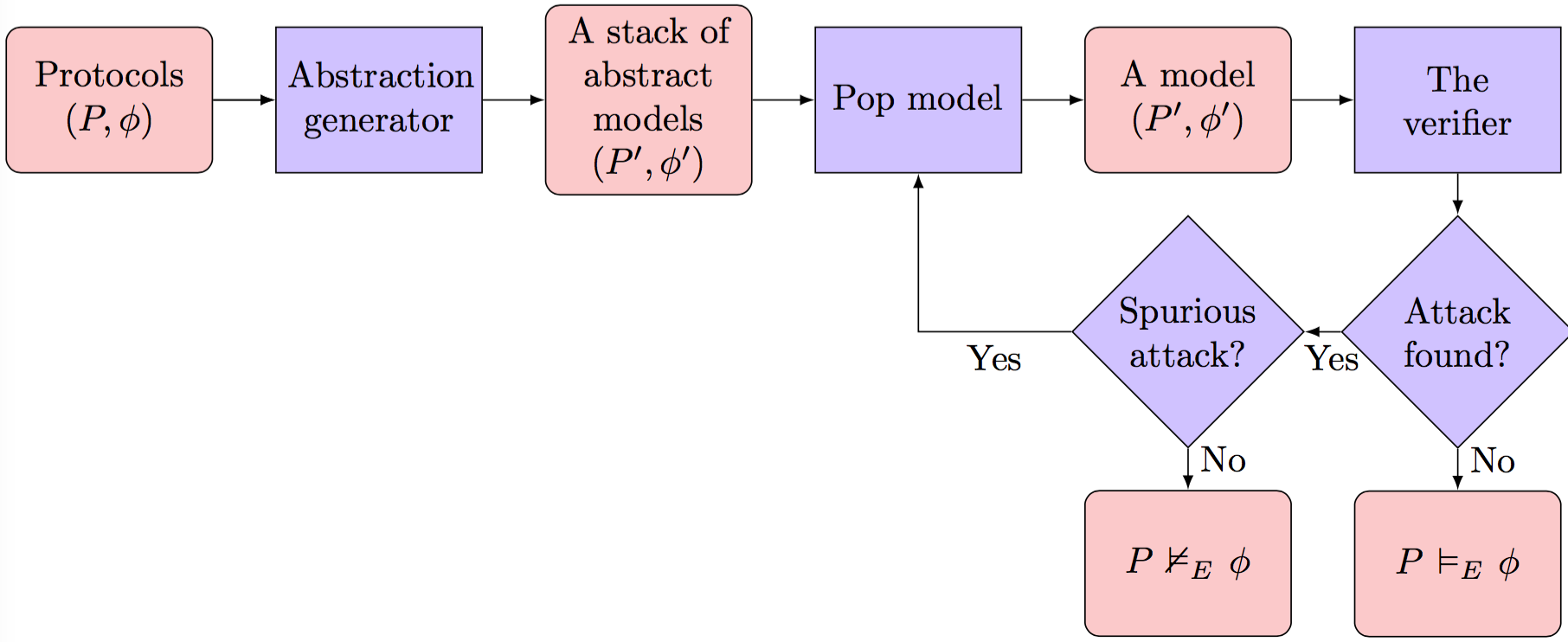
An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture | EURASIP Journal on Wireless Communications and Networking | Full Text